We get a lot of
pages when searching for data from google.com. Dorks are a simple way of
getting expected data from the search engine.
What's a Dork?
A normal search
string results in millions of results. A user mostly views not more than 4-5 pages. Google is but a search engine and
not a human!
However, there are ways to get results very
specific or close to your search query and requirements. Google allows a user to make use of keywords
in combination with the search strings to get very effective output.
Some of the most
commonly used keywords are as below:
[define:]
returns the pages containing the search string in exact order.
And mark the difference in the number of returned results for the define search:
This one is interesting to note. In security if you are into OSINT and people search, define gives precise results. Also good for tracing problem solving methods if you have the result [and want to learn ;)]
[Allintitle, intitle:]
All pages having the search strings mentioned with 'intitle' are returned. Often used when we need to search pages serving a certain feature or providing a certain functionality like:
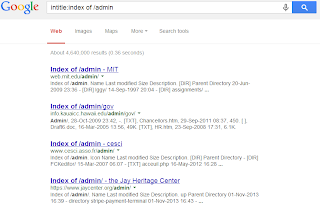
We find an interesting result for the most searched items for this dork:
' Index of' is an excellent string to use when searching for any kind of directory indexing and related issues. It may open the door for numerous entry points and back-doors [to information] we never thought existed.
And so are others.
[Allinurl, inurl:] Returns searches for all urls bearing the string specified. This can give us pages having the same exact string in the url.
So in case we want to find all login pages written in php-
inurl:login.php
Hence, we could use this to get typically vulnerable pages for a given framework/platform.
Some other interesting queries and results are given below:
inurl:oraweb
Lists all sites having oraweb in their url and hence mostly those using oracle web server.
[site:] This is to specify the site we want the information from/about.
E.g. intitle:login site:facebook.com >> Gives us all pages belonging to facebook.com and having 'login' in title (so user login, admin, developer, troubleshooting, .... the list goes on)
There are other advanced dorks to enhance searching through google. I have listed a few below:
*** intitle:"Test Page for Apache" "It Worked!"
Lists all pages having test pages from Apache installation exposed.
***inurl:updown.php | intext:"Powered by PHP Uploader Downloader"
An example of pages with known vulnerabilities - these pages may have an 'upload shell issue'
http://www.exploit-db.com/exploits/10719/
*** "Powered By: Simplicity oF Upload" inurl:download.php | inurl:upload.php
*** ext:xml ("proto='prpl-'" | "prpl-yahoo" | "prpl-silc" | "prpl-icq")
Find account details from Pidgin Users.
Note the use of ext:xml, similarly we can specify exact extensions for the files being searched.
Similary we can use filetype to specify the kind/type of file
*** filetype:config inurl:web.config inurl:ftp
Finds information of MySqlServer in web.config through ftp..
filetype:cfg > for config files
filetype:sql > sql back ups
filetype:reg > registry entries
filetype:ini, log .. and so on...
Acknowledgment: I have referred to the below websites for this post. I recommend them for extensive information on google dorking and techniques for effective penetration testing.
http://www.exploit-db.com/google-dorks/
http://www.hackersforcharity.org/ghdb/
Important: The information given above is strictly for learning purposes and should not be used for gaining unauthorized access to any host on the internet.








No comments:
Post a Comment