This is a basic post to demonstrate post exploitation techniques in a windows victim using basic windows commands. The exploit being run in this case is the netapi exploit. It is highly recommended to understand the where the flaw is in the system and mechanism used by the exploit code to run the payload and the odds there upon.
MS 08-067: Vulnerability in Server Service Could Allow Remote Code Execution
This security update resolves a privately reported vulnerability in the
Server service. The vulnerability could allow remote code execution if
an affected system received a specially crafted RPC request. On
Microsoft Windows 2000, Windows XP, and Windows Server 2003 systems, an
attacker could exploit this vulnerability without authentication to run
arbitrary code.
Target: A windows XP SP3 basic machine
Victim: 192.168.78.132 [Windows XP]
Attacker: 192.168.78.135 [Kali]
As a first step, I scanned the victim for open ports to check which services are running on the victim and if any of those could be exploited.
After some searches, I found the RPC service vulnerable to the above mentioned netapi exploit. Remember to check out the OS platform and version details to streamline and use the right exploit.
This one is also present in metasploit, so to keep matters simple I chose to use run it using the msf framework. The payload details are given below:
PAYLOAD: bind_shell_tcp
[We may take up metasploit basics in later posts]
Running the Exploit:
Once the right exploit and payload are identified, running the exploit on the target using metasploit, is kinda short and sweet. I set the below options for netapi.
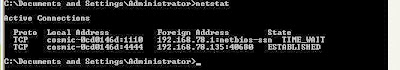
The attack successfully launched me into the victim shell. I confirmed the IP just to be sure :)
On the other side the I checked the connection was established. More often than not, in a realistic attack scenario these connections are weak and may need running the exploit a couple of times to stabilize enough for an extended post exploitation.
Post Exploitation: IsLand NaTi0n
The first question we have on mind after a hard earned battle is - what next!
Its not a question, its a huge possibility. Although with the advent of msf/metasploit, this one thing has been kind of automated (using meterpreter with some cool post exploitation commands and partly using payloads), I would encourage the reader to be armed with basic but necessary post exploitation OS commands. Meterpreter is not always an option ;)
Some basic commands which we always use are:
cd
dir
copy/del/mkdir/move
and others ..
Some typically of use are given below:
Informational:
* systeminfo: Displays detailed configuration information about a computer and its operating system, including operating system configuration, security information, product ID, and hardware properties, such as RAM, disk space, and network cards.
systeminfo[.exe] [/s Computer [/u Domain\User [/p Password]]] [/fo {TABLE|LIST|CSV}] [/nh]
systeminfo[.exe] [/s Computer [/u Domain\User [/p Password]]] [/fo {TABLE|LIST|CSV}] [/nh]
A sample response for the above victim shows
Host Name: COMP-0CD0146D
OS Name: Microsoft Windows XP Professional
OS Version: 5.1.2600 Service Pack 3 Build 2600
OS Manufacturer: Microsoft Corporation
OS Configuration: Standalone Workstation
OS Build Type: Uniprocessor Free
Registered Owner: COMP
*
OS Name: Microsoft Windows XP Professional
OS Version: 5.1.2600 Service Pack 3 Build 2600
OS Manufacturer: Microsoft Corporation
OS Configuration: Standalone Workstation
OS Build Type: Uniprocessor Free
Registered Owner: COMP
*
*
NetWork Card(s): 1 NIC(s) Installed.
[01]: VMware Accelerated AMD PCNet Adapter
Connection Name: Local Area Connection
DHCP Enabled: Yes
DHCP Server: 192.168.78.254
IP address(es)
[01]: 192.168.78.132
NetWork Card(s): 1 NIC(s) Installed.
[01]: VMware Accelerated AMD PCNet Adapter
Connection Name: Local Area Connection
DHCP Enabled: Yes
DHCP Server: 192.168.78.254
IP address(es)
[01]: 192.168.78.132
* tasklist :Displays a list of applications and services with their Process ID (PID) for all tasks running on either a local or a remote computer.
Administration:
*gpresult: Displays Group Policy settings and Resultant Set of Policy (RSOP) for a user or a computer.
*gpupdate : The gpupdate command is used to update Group Policy settings.
net user [UserName [Password | *] [options]] [/domain]
net user [UserName {Password | *} /add [options] [/domain]]
net user [UserName [/delete] [/domain]]
Network:
*ipconfig: The ipconfig command is used to display detailed IP information for each network adapter utilizing TCP/IP. The ipconfig command can also be used to release and renew IP addresses on systems configured to receive them via a DHCP server.
*netsh: Netsh is a command-line scripting utility that allows you to, either locally or remotely, display or modify the network configuration of a computer that is currently running.Netsh also provides a scripting feature that allows you to run a group of commands in batch mode against a specified computer. Netsh can also save a configuration script in a text file for archival purposes or to help you configure other servers.
firewall - Changes to the `netsh firewall' context.
[ http | interface | ipsec | lan | namespace | netio | winhttp | winsock | wlan
[ http | interface | ipsec | lan | namespace | netio | winhttp | winsock | wlan
set - Updates configuration settings.
show - Displays information.
show - Displays information.
The net commands: Numerous commands in this suite. Do check out each one. Listing a couple of them here.
* net view ->Displays a list of domains, computers, or resources that are being shared by the specified computer. Used without parameters, net view displays a list of computers in your current domain.
net view [\\ComputerName] [/domain[:DomainName]]
* net use -> Connects a computer to or disconnects a computer from a shared resource, or displays information about computer connections. The command also controls persistent net connections. Used without parameters, net use retrieves a list of network connections.
net use [DeviceName [/home[{Password | *}] [/delete:{yes | no}]]
* net view ->Displays a list of domains, computers, or resources that are being shared by the specified computer. Used without parameters, net view displays a list of computers in your current domain.
net view [\\ComputerName] [/domain[:DomainName]]
* net use -> Connects a computer to or disconnects a computer from a shared resource, or displays information about computer connections. The command also controls persistent net connections. Used without parameters, net use retrieves a list of network connections.
net use [DeviceName [/home[{Password | *}] [/delete:{yes | no}]]
*arp
* nbtstat
Displays NetBIOS over TCP/IP (NetBT) protocol statistics, NetBIOS name tables for both the local computer and remote computers, and the NetBIOS name cache. Nbtstat allows a refresh of the NetBIOS name cache and the names registered with Windows Internet Name Service (WINS). Used without parameters, nbtstat displays help.
The nbtstat command is used to show TCP/IP information and other statistical information about a remote computer.
NBTSTAT [ [-a RemoteName] [-A IP address] [-c] [-n] [-r] [-R] [-RR] [-s] [-S] [interval] ]
RemoteName Remote host machine name.
IP address Dotted decimal representation of the IP address.
The nbtstat command is used to show TCP/IP information and other statistical information about a remote computer.
NBTSTAT [ [-a RemoteName] [-A IP address] [-c] [-n] [-r] [-R] [-RR] [-s] [-S] [interval] ]
RemoteName Remote host machine name.
IP address Dotted decimal representation of the IP address.
* route
Registry: To query the registry or change DWORD values
Adds, changes, and displays registry subkey information and values in registry entries.
REG Operation [Parameter List]
Operation [ QUERY | ADD | DELETE | COPY |
SAVE | LOAD | UNLOAD | RESTORE |
COMPARE | EXPORT | IMPORT ]
REG Operation [Parameter List]
Operation [ QUERY | ADD | DELETE | COPY |
SAVE | LOAD | UNLOAD | RESTORE |
COMPARE | EXPORT | IMPORT ]
Transfer commands: to transfer tools, binaries, files, etc..
* ftp: The ftp command can used to transfer files to and from another computer. The remote computer must be operating as an FTP server
tftp [-i] [Host] [{get | put}] [Source] [Destination]
Running those tools >>
* runas
Allows a user to run specific tools and programs with different permissions than the user's current logon provides.
Allows a user to run specific tools and programs with different permissions than the user's current logon provides.
* rexec
Runs commands on remote computers running the Rexec service (daemon). The rexec command authenticates the user name on the remote computer before executing the specified command. Windows XP and Windows 2000 do not provide the Rexec service. Used without parameters, rexec displays help.
rexec [Host] [-l UserName] [-n] [Command]
Miscellaneous
Type: Type out a file contents
Edit: Create, edit files.
* expand: The expand command is used to extract a single file or a group of files from a compressed file.
The expand command is not available in 64-bit versions of Windows XP.
* find: The find command is used to search for a specified text string in one or more files.
* findstr: The findstr command is used to find text string patterns in one or more files.
Note: The reader is encouraged to use the help options to explore further information regarding the system.
Acknowledgement: All definitions have been taken from microsoft's documentation- http://www.microsoft.com/resources/documentation/windows/xp/all/proddocs/en-us/ntcmds.mspx?mfr=true
* expand: The expand command is used to extract a single file or a group of files from a compressed file.
The expand command is not available in 64-bit versions of Windows XP.
* find: The find command is used to search for a specified text string in one or more files.
* findstr: The findstr command is used to find text string patterns in one or more files.
Query Commands
* query user: Displays information about user sessions on a terminal server.
query user [{UserName|SessionName|SessionID}] [/server:ServerName]
query user [{UserName|SessionName|SessionID}] [/server:ServerName]
* query termserver: Displays a list of all terminal servers on the network.
* query session:
Displays information about sessions on a terminal server. The list
includes information not only about active sessions but about other
sessions that the server runs.
* query process:
Displays information about processes running on a terminal server. You
can use this command to find out which programs a specific user is
running, and also which users are running a specific program.
Note: The reader is encouraged to use the help options to explore further information regarding the system.
Acknowledgement: All definitions have been taken from microsoft's documentation- http://www.microsoft.com/resources/documentation/windows/xp/all/proddocs/en-us/ntcmds.mspx?mfr=true








No comments:
Post a Comment